DESIGN
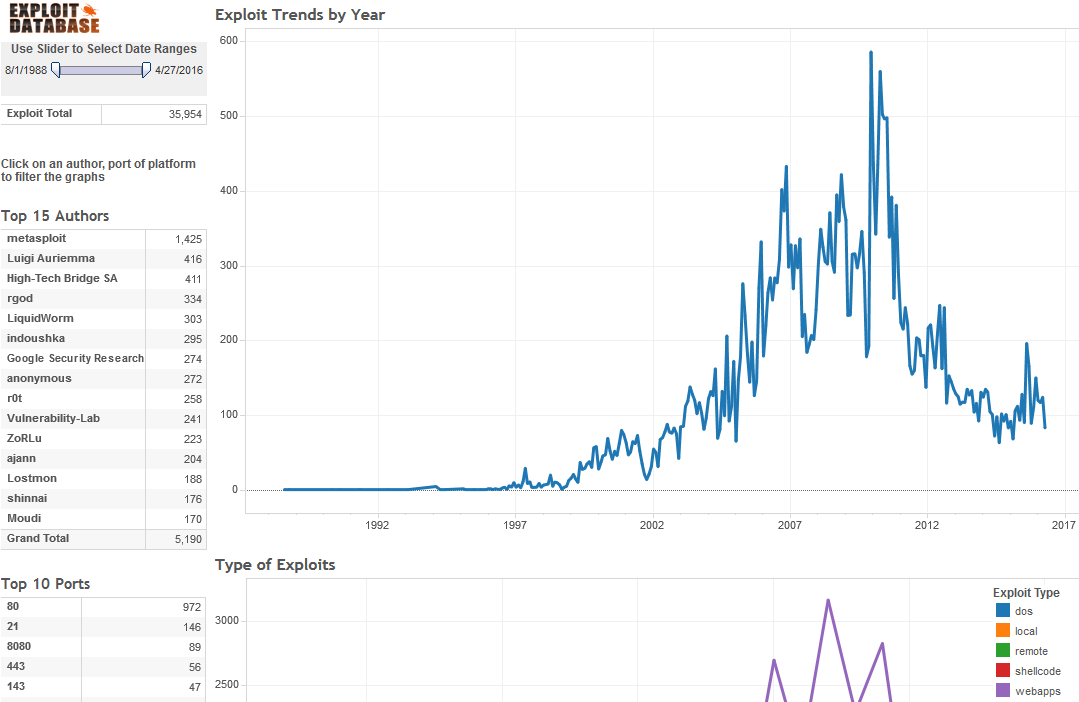
Computer Exploit Database Visualized
The ultimate archive of public exploits to corresponding vulnerable software; developed by penetration testers and vulnerability.
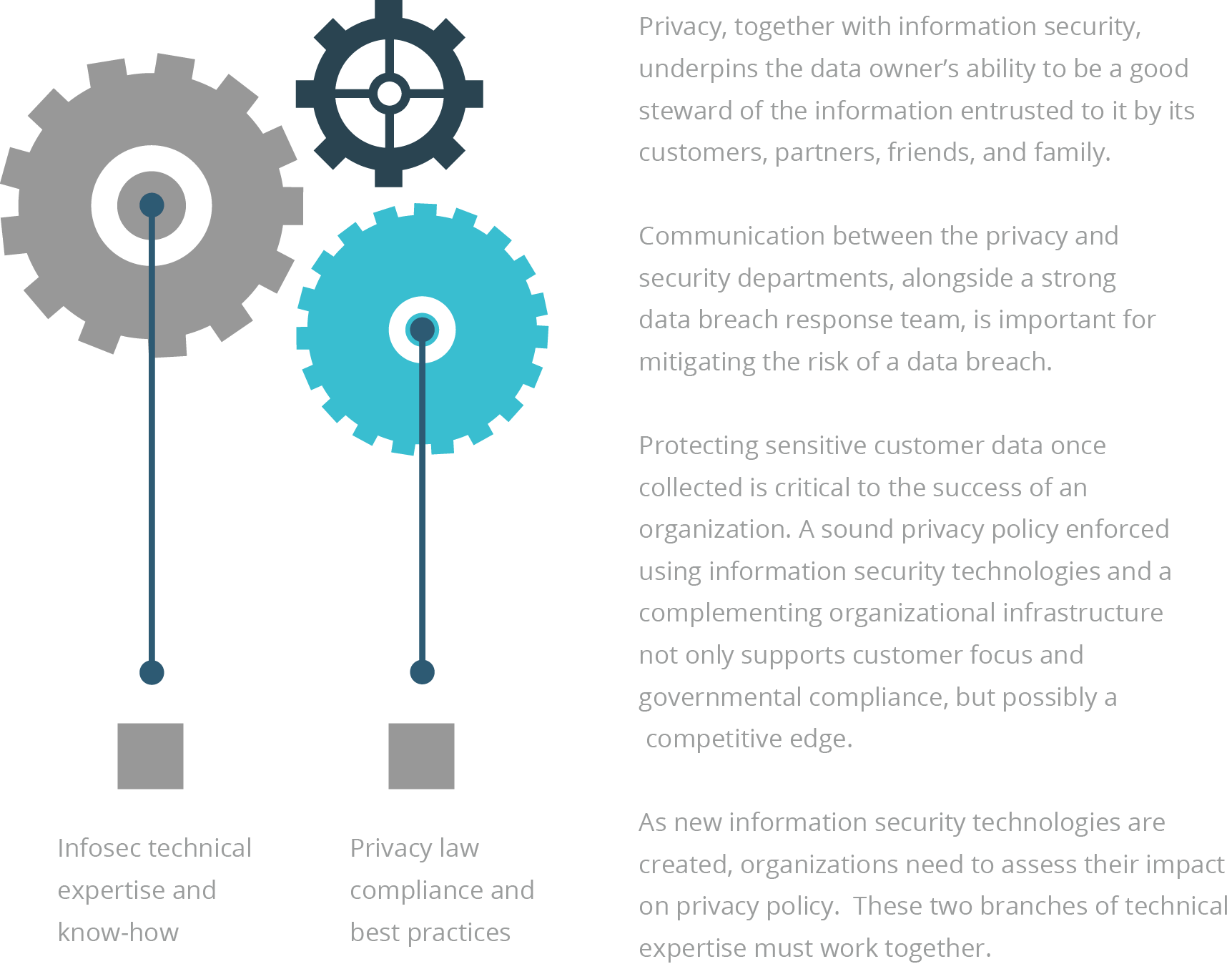
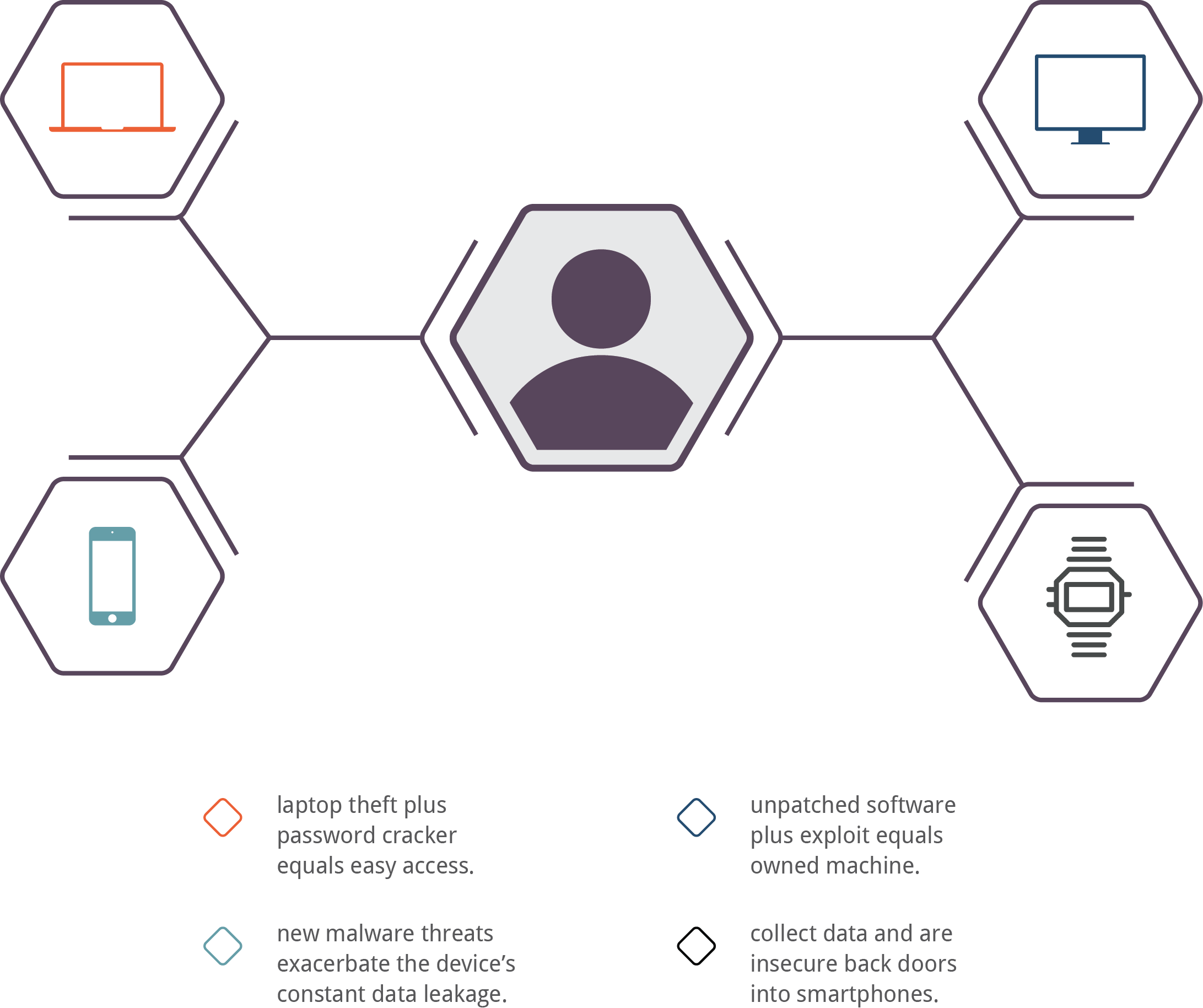
Privacy and Infosec Working Together
As new information security technologies are created, organizations need to assess their impact on privacy policy.
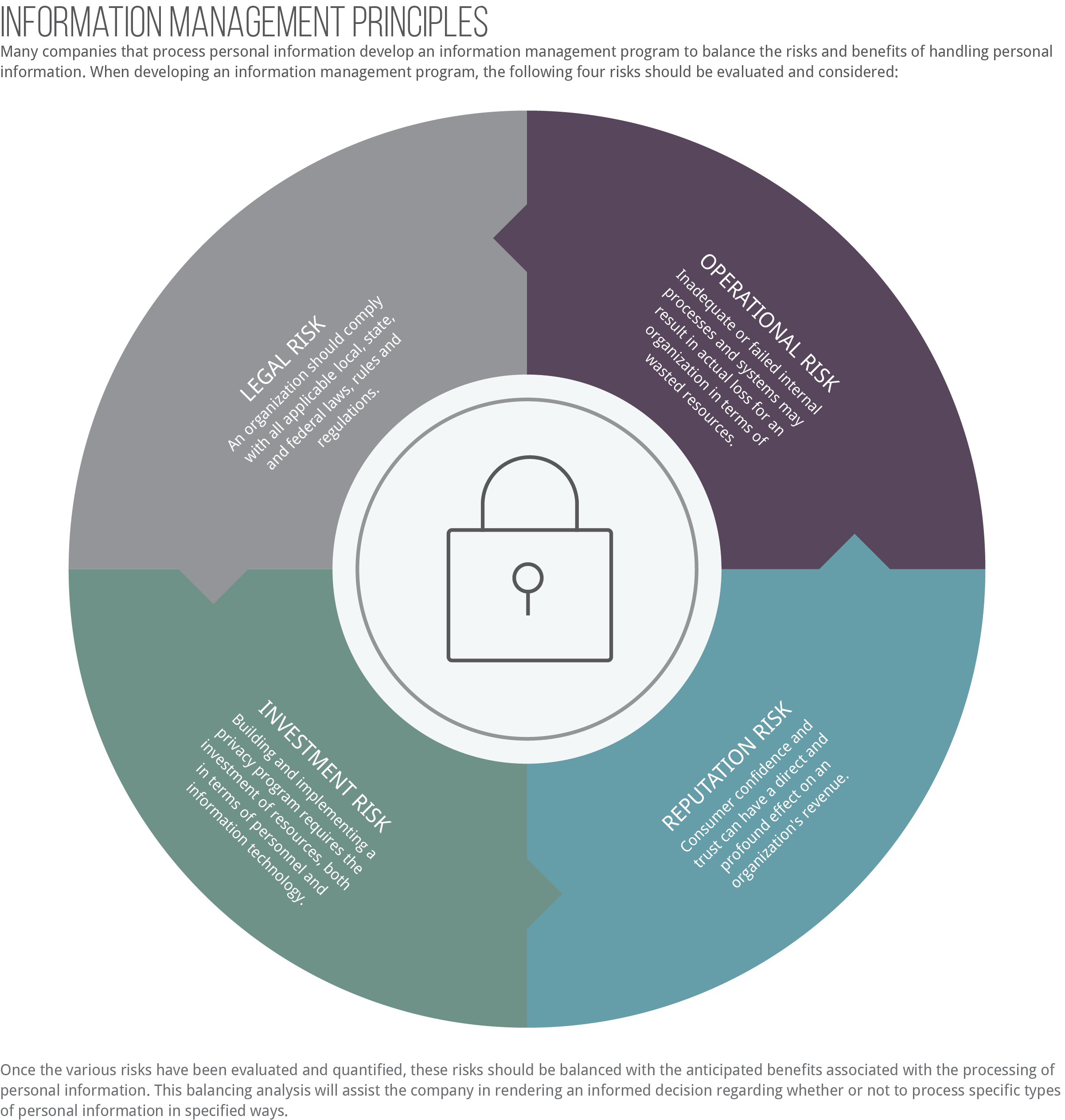
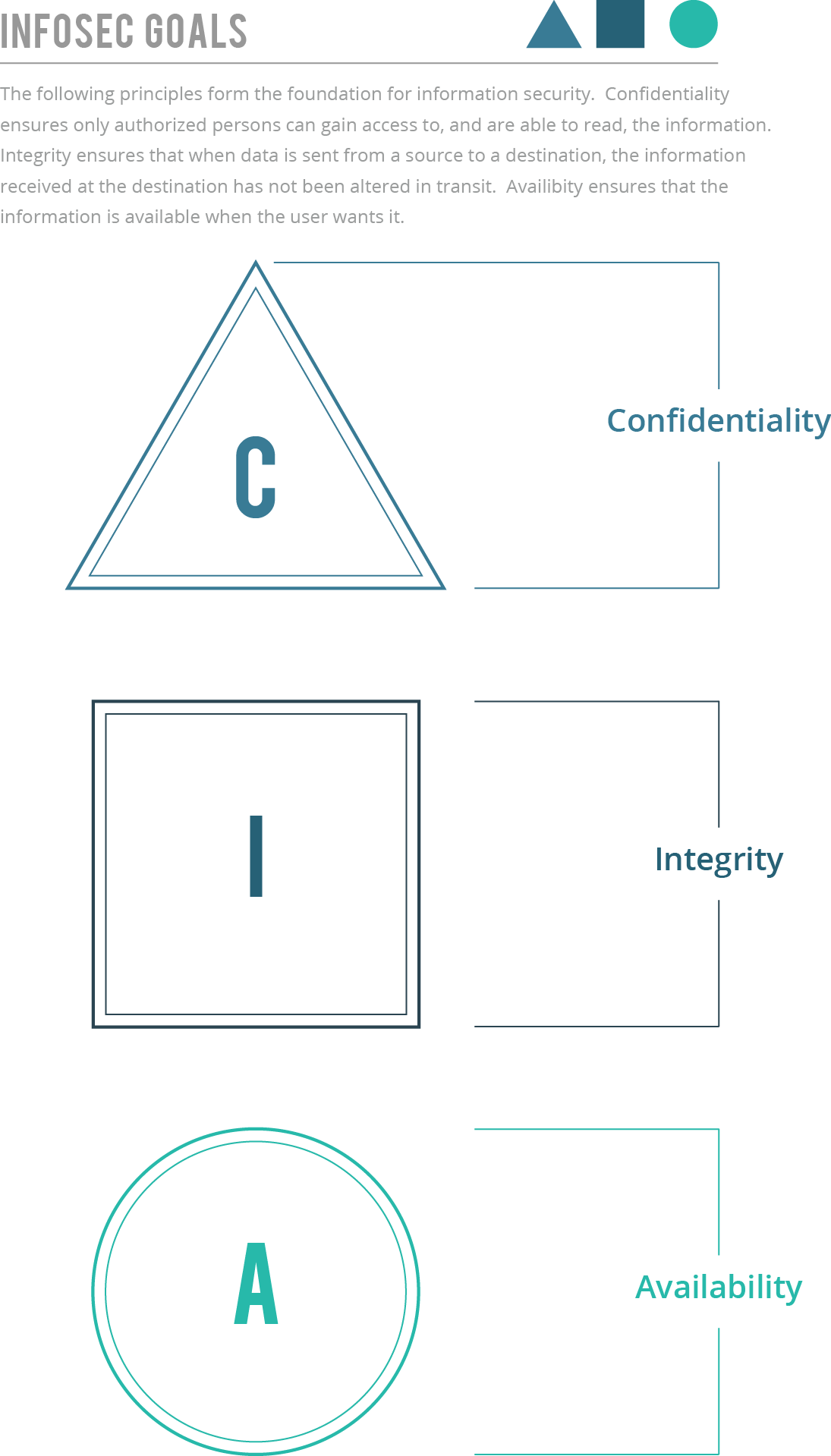
Information Management Risk Assessment
An information management program is simply a tool that provides a framework for making well-reasoned decisions regarding the company's processing of personal information.
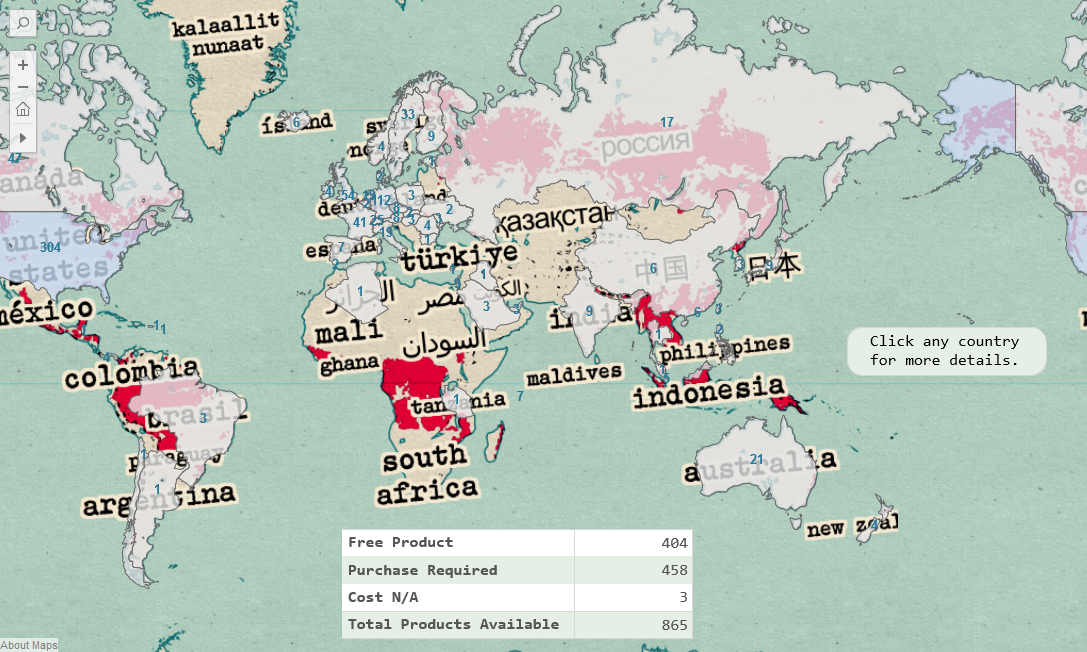
Tableau: Worldwide Encryption Products
The largest database of encryption products available around the world.
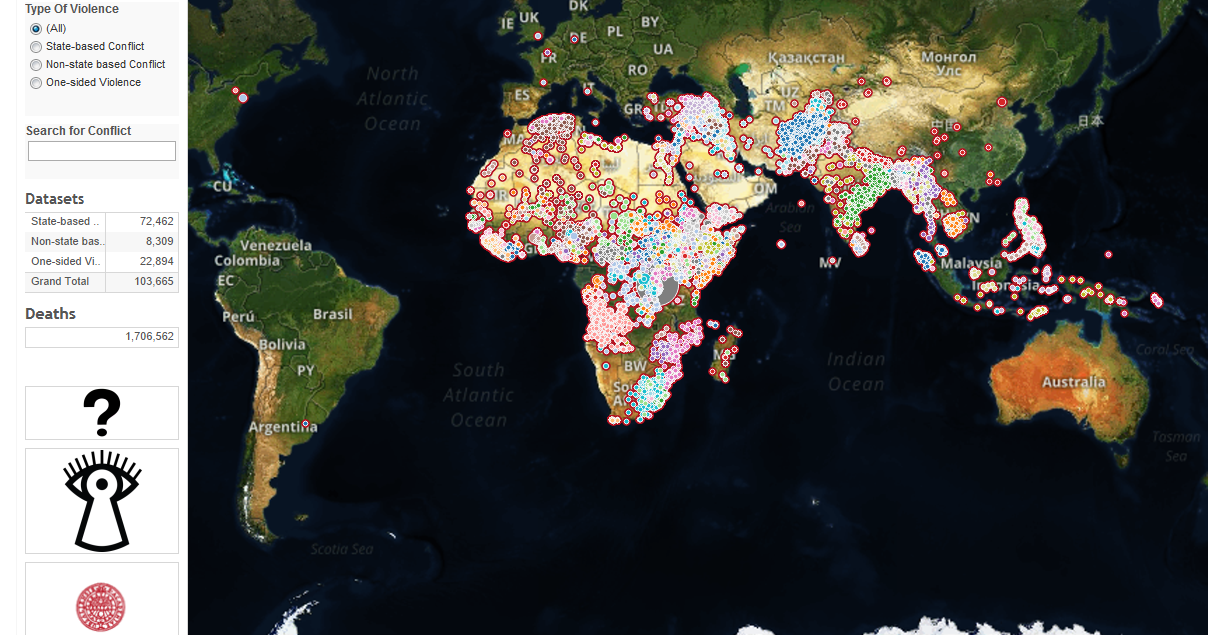
Tableau Viz: Global Instances of Violence (1989-2014)
With 103,665 conflict entries, the Uppsala Conflict Data Program Conflict Map provides detailed info including exact location of each conflict.
Business Card Mockup
I find mockups are an interesting way to present material in sometimes out of context designs.
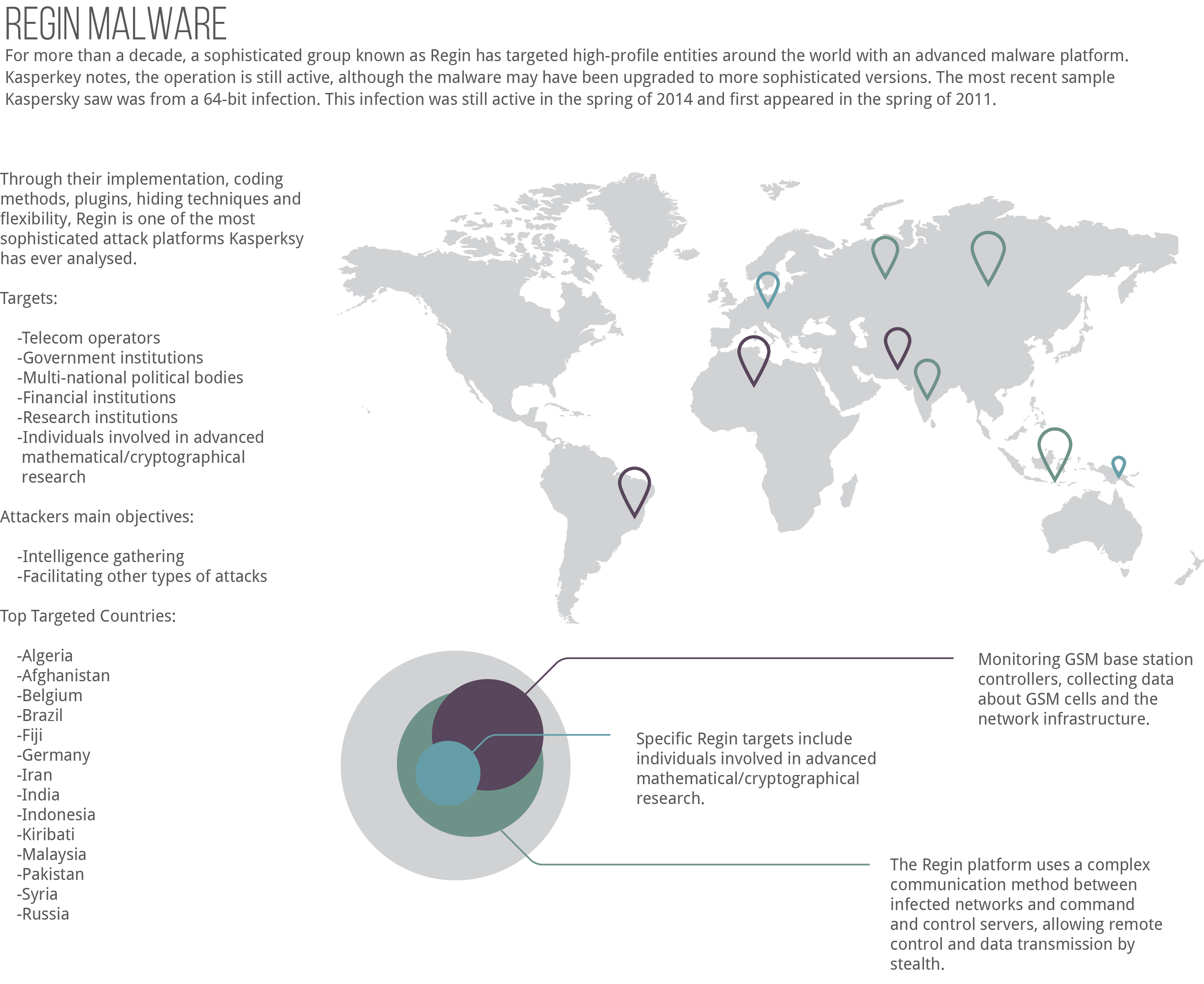
Regin Malware Infographic
Through their implementation, coding methods, plugins, hiding techniques and flexibility, Regin is one of the most sophisticated attack platforms Kasperksy has ever analysed.
Wiretap and Surveillance Poster
propaganda poster highlighting illegal and legal state sponsored wiretapping and surveillance.
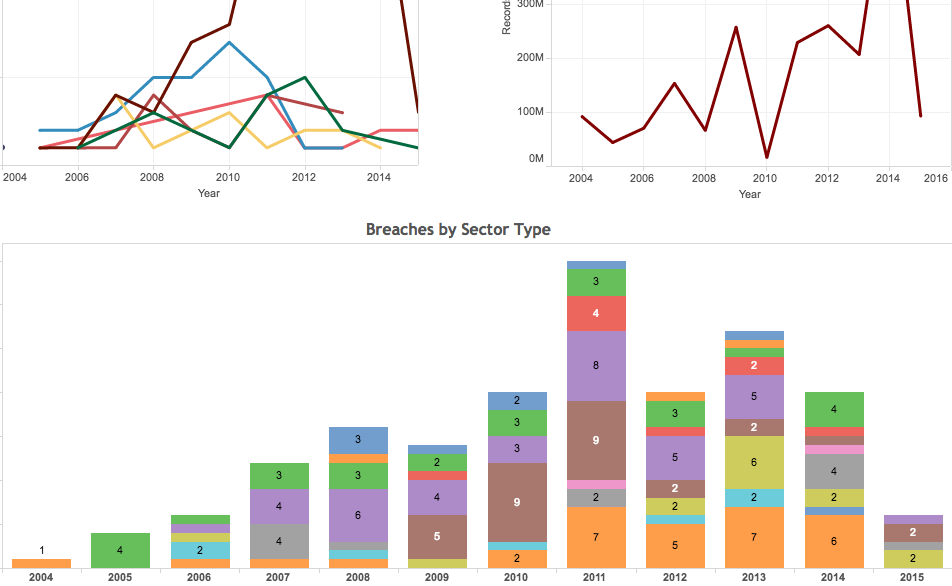
Tableau Interactive: Significant Data Breaches from 2004 to Jan 2015
This interactive data visualization examines significant data breaches since 2004.
Tableau Interactive: All HIPAA Data Breaches since 2009
Data Breaches in U.S. Affecting 500 or More Individuals (2009-2015)
Protect Your Privacy Poster
Our data is constantly being tracked, surveilled, sold, stolen, and compromised. We would be concerned if someone we didn't know had VHS tapes of our movements, yet we freely give away our location, data, and personal information. Governments, corporations and unsavory characters compile our data into profiles - they have tapes and tapes of information on us. Protect your privacy.
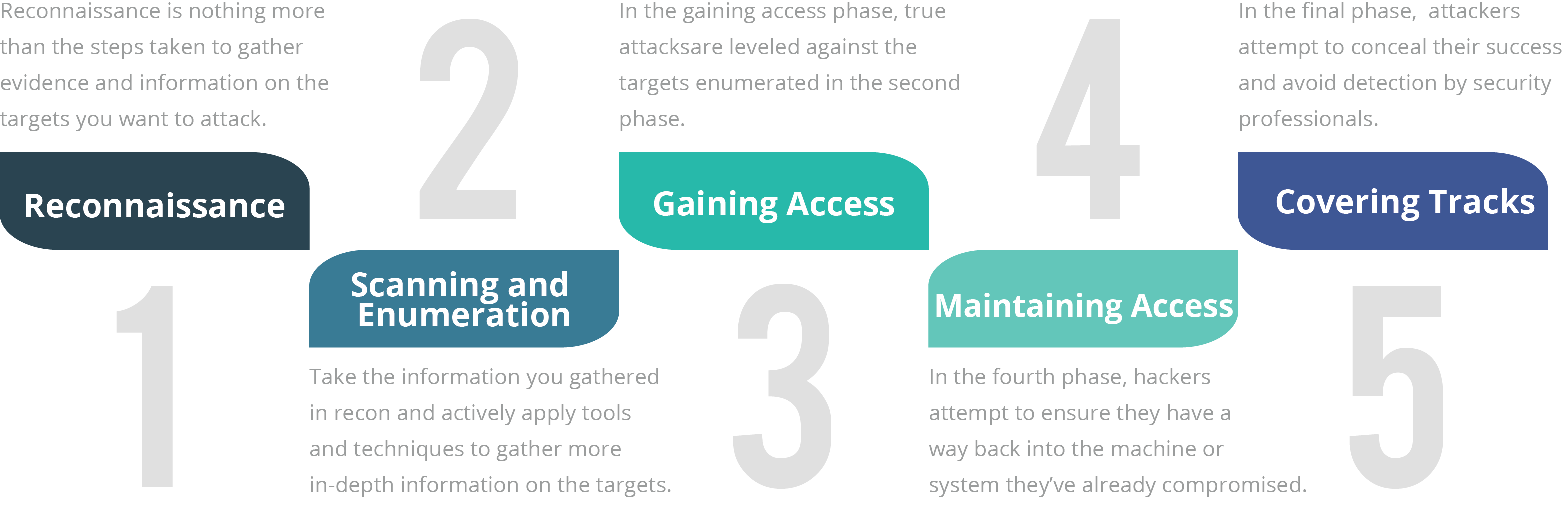
Ethical Hacking Phases
Although there are many different terms for these phases and some of them run concurrently and continuously throughout a test, EC-Council has defined the standard hack as having five phases. Whether the attacker is ethical or malicious, these five phases capture the full breadth of the attack.
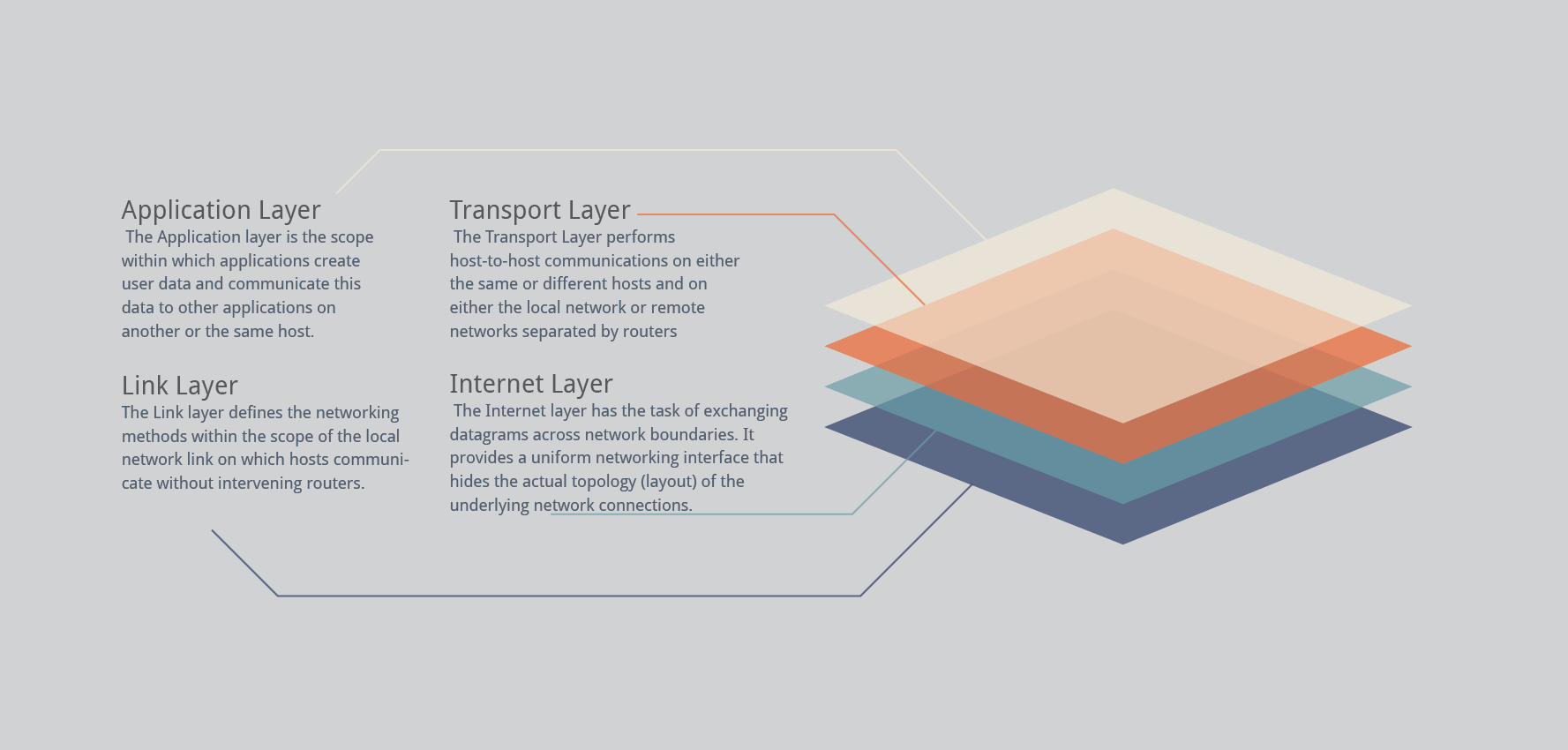
TCP/IP Protocol Suite
TCP/IP (transmission control protocol/Internet protocol) is the suite of communications protocols that is used to connect hosts on the Internet and on most other computer networks as well. It is also referred to as the TCP/IP protocol suite and the Internet protocol suite.
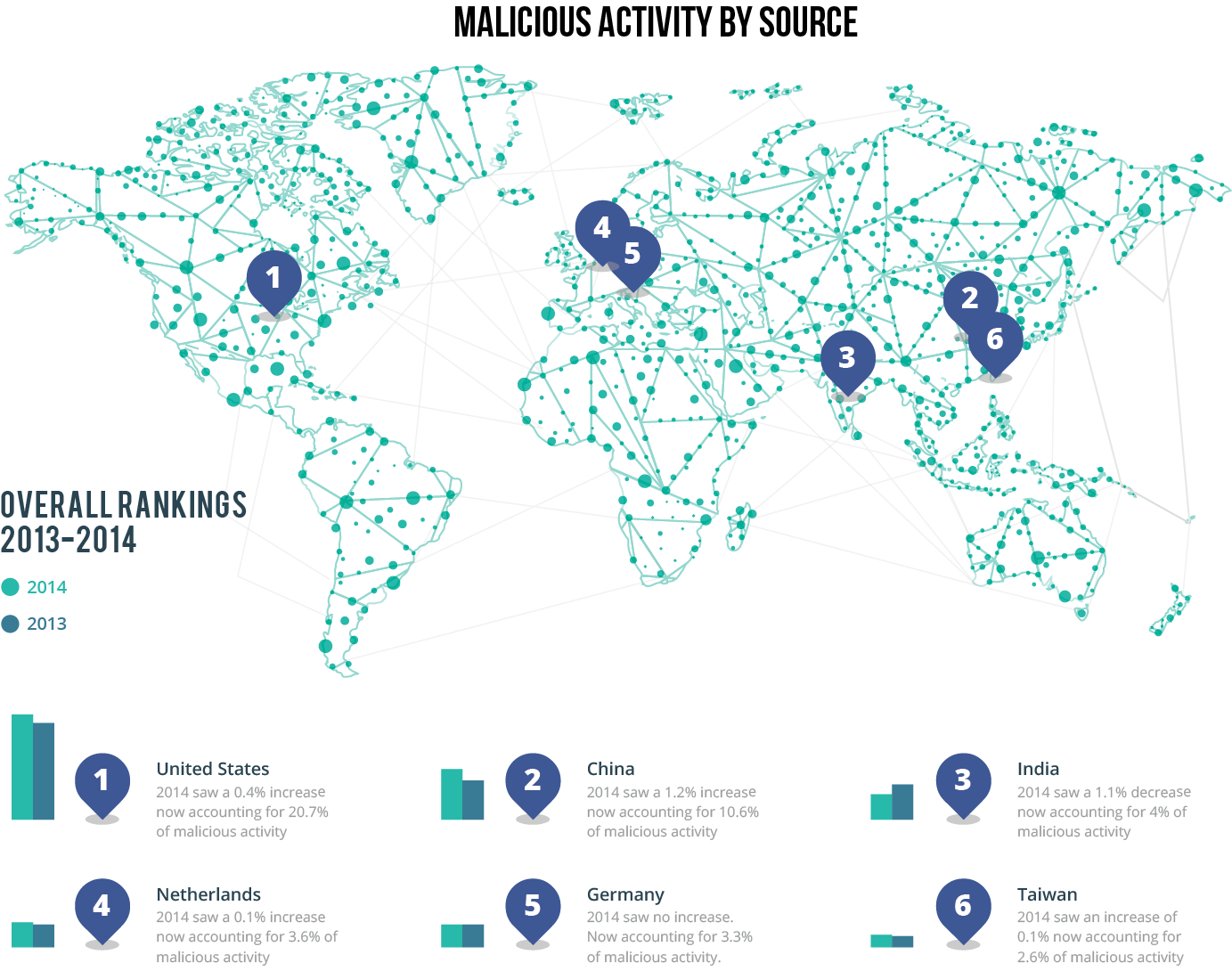
Malicious Activity by Source: Overall Rankings 2013-2014
An Infographic map outlining the six top countries where malicious activities occur. Includes percentages for 2013-2014. Source: Symantec
Reasonable Expectation of Privacy Poster
I created this poster so that no one can enter your room without your permission. In some circumstances, this may not be bulletproof (dorms, hospitals, mental hospitals or other legally contracted space), but it will clearly demarcate your space as private and needing your permission to enter.
Government Surveillance Propaganda Poster
Retro style propaganda poster featuring the U.S. Government surveillance state. Textured to look like an old poster from the 1950's era.
infosec.lawyer Logo Design
We have a key hole and an eye. This speaks to security and to privacy - we want to keep something locked. However, the eye looks through the key hole to spy, to discover, to learn, to penetrate the cone of privacy.