PENTEST
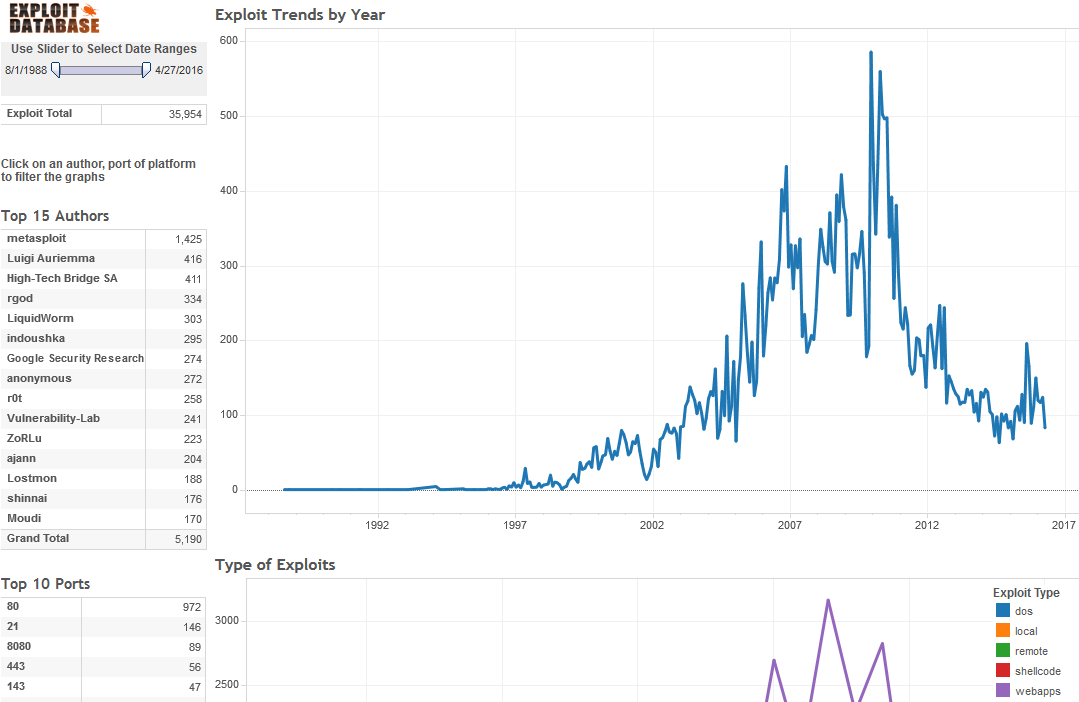
Computer Exploit Database Visualized
The ultimate archive of public exploits to corresponding vulnerable software; developed by penetration testers and vulnerability.
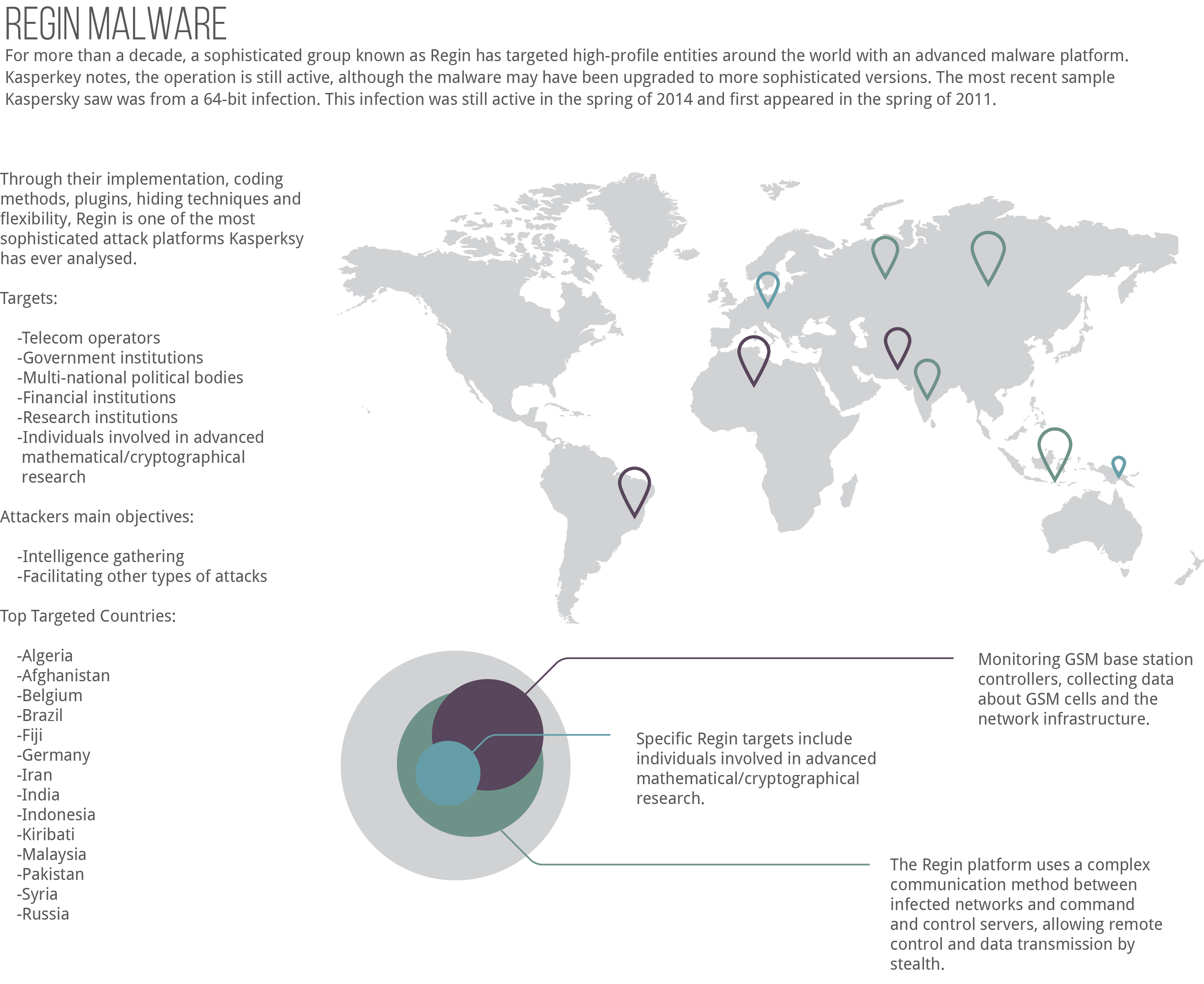
Regin Malware Infographic
Through their implementation, coding methods, plugins, hiding techniques and flexibility, Regin is one of the most sophisticated attack platforms Kasperksy has ever analysed.
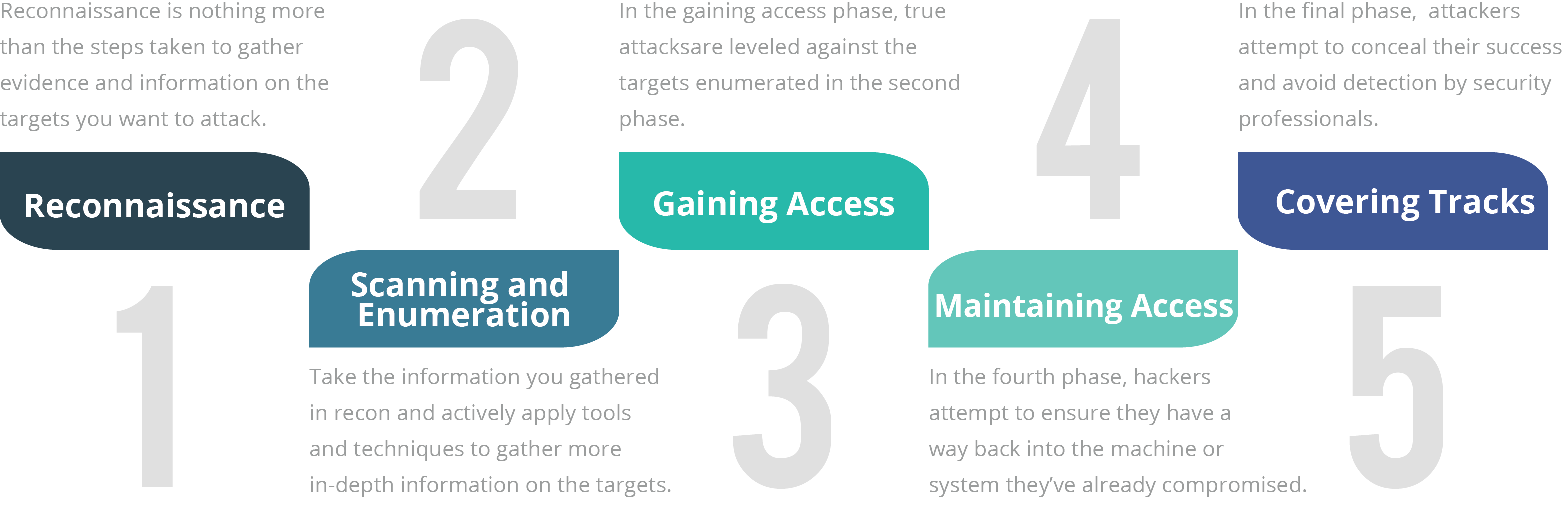
Ethical Hacking Phases
Although there are many different terms for these phases and some of them run concurrently and continuously throughout a test, EC-Council has defined the standard hack as having five phases. Whether the attacker is ethical or malicious, these five phases capture the full breadth of the attack.